Staying Ahead of the Curve: 6 Top Legal Tech Trends to Watch in 2023
ARMA International
AUGUST 7, 2023
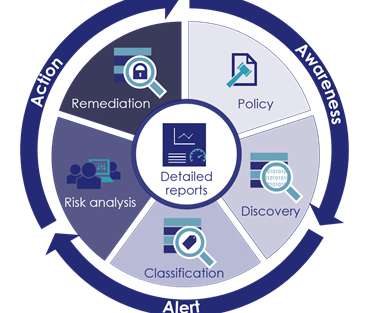
These include artificial intelligence (AI), hybrid and remote work collaboration, cloud, workflow automation and customization, mail processing and digitization, and security and data privacy. Are their levels of security and privacy protocols leaving them vulnerable to breaches and cyberattacks?


















Let's personalize your content