GDPR Compliance Obligations: The relationship between Data Controllers and Third-Party Processors
AIIM
JULY 24, 2018
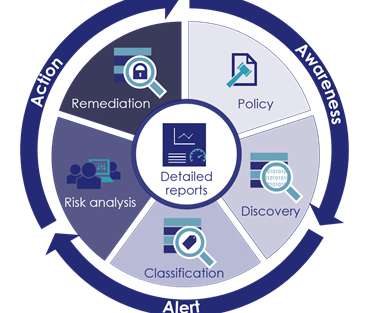
This is the 11th post in a series on privacy by Andrew Pery. You might also be interested in: The Re-Permissioning Dilemma Under GDPR. Data Privacy and Open Data: Secondary Uses under GDPR. Three Critical Steps for GDPR Compliance. Mitigate Data Privacy and Security Risks with Machine Learning.














Let's personalize your content