Twitter, Facebook, and Instagram blocked in Turkey as Idlib military crisis escalates
Security Affairs
FEBRUARY 28, 2020
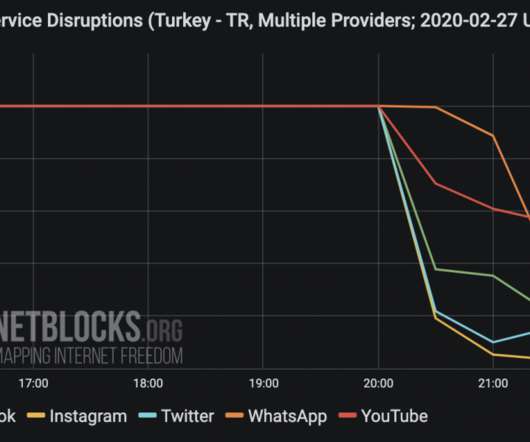
Network data collected by the NetBlocks internet observatory confirm that Turkey has blocked access to social media as Idlib military crisis escalates. Major social media platforms, including Twitter, Facebook, and Instagram, were not reachable since 11:30 p.m. local time (8:30 p.m. ” reported NetBlocks. It's 5:30 a.m.















Let's personalize your content