Researchers created a PoC for Apache OFBiz flaw CVE-2023-51467
Security Affairs
JANUARY 12, 2024
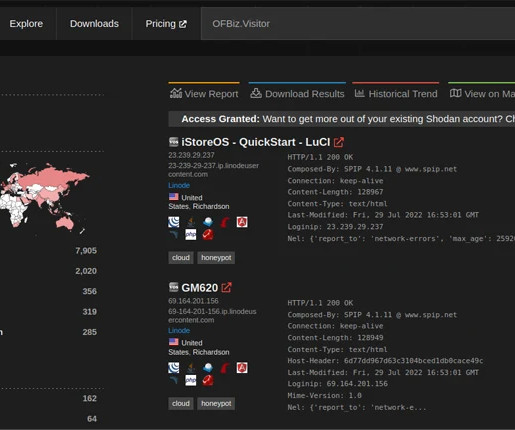
Researchers from cybersecurity firm VulnCheck have created a proof-of-concept (PoC) exploit code for the recently disclosed critical flaw CVE-2023-51467 (CVSS score: 9.8) The experts pointed out that almost all of these are honeypots. in the Apache OfBiz. reads the report published by SonicWall.













Let's personalize your content