Chinese actor ‘Unfading Sea Haze’ remained undetected for five years
Security Affairs
MAY 23, 2024
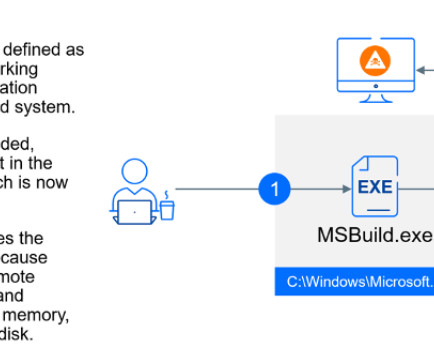
Upon receiving a request, it executes the encoded JavaScript code using the Microsoft.JScript library. Our investigation also uncovered two additional variations that utilize cloud storage services for communication instead of direct HTTP requests. . “SharpJSHandler operates by listening for HTTP requests.
















Let's personalize your content