Private 5G Networks: Thales and Celona Collaborate to Bring Security and Performance to a Modern World
Thales Cloud Protection & Licensing
FEBRUARY 19, 2023
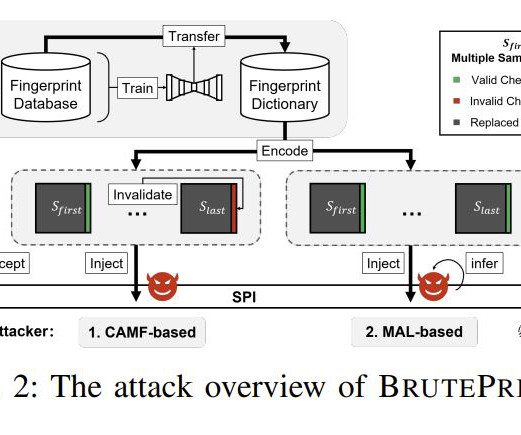
These private mobile networks are gaining significant traction in manufacturing, energy, government, logistics, and warehousing verticals. To start, Thales offers full-line rate encryption at high speeds - up to 100Gbps - with nearly zero jitters and ultra-low latency rates. This is driving a strong demand for private mobile networks.













Let's personalize your content