Updated Kmsdx botnet targets IoT devices
Security Affairs
AUGUST 28, 2023
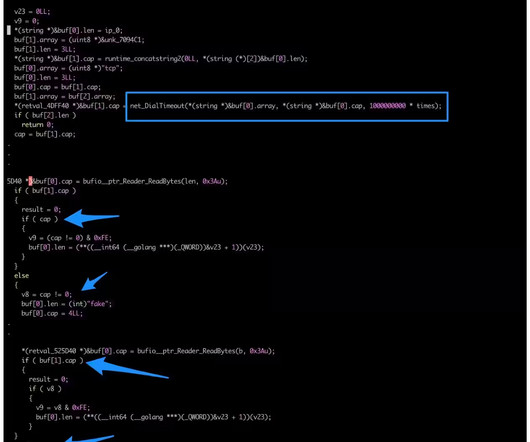
The malicious code was used in attacks targeting multiple sectors including the gaming industry, technology industry, and luxury car manufacturers. The bot targets private gaming servers, cloud hosting providers, and certain government and educational sites. ” reads the report published by Akamai.


















Let's personalize your content