Weakness at the Network Edge: Mandiant Examines 2022’s Zero-Day Exploits
eSecurity Planet
MARCH 27, 2023
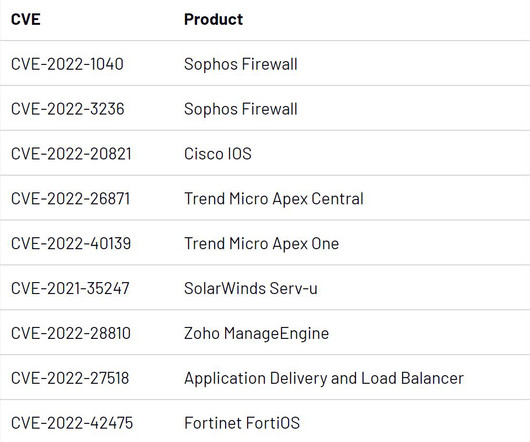
Enterprise IT, network and security product vulnerabilities were among those actively exploited in zero-day attacks last year, according to a recent Mandiant report. Also read: Network Protection: How to Secure a Network Follina State-Sponsored Campaigns CVE-2022-30190, a.k.a.











Let's personalize your content