Experts spotted a backdoor that borrows code from CIA’s Hive malware
Security Affairs
JANUARY 16, 2023
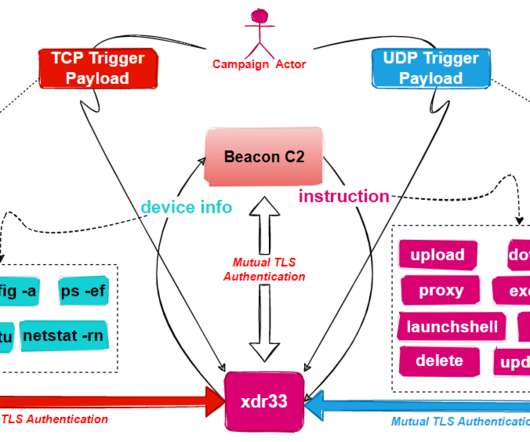
One of the 360Netlab’s honeypot caught a suspicious ELF file on October 2021, the experts reported that the malware was spread by exploiting F5 zero-day exploit. xdr33 uses XTEA or AES algorithm for traffic encryption and uses SSL with Client-Certificate Authentication mode enabled to protect the traffic.





















Let's personalize your content