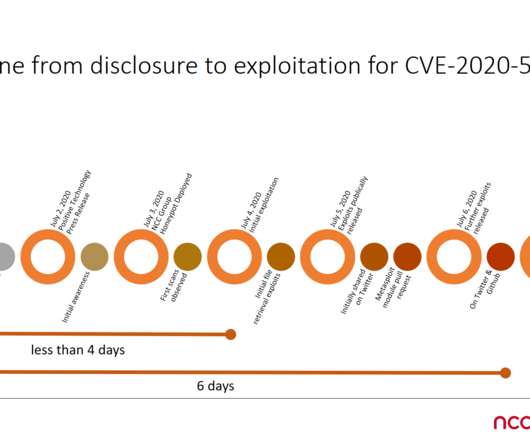
Threat actors found a way to bypass mitigation F5 BIG-IP CVE-2020-5902 flaw
Security Affairs
JULY 8, 2020
This vulnerability allows for unauthenticated attackers, or authenticated users, with network access to the TMUI, through the BIG-IP management port and/or Self IPs, to execute arbitrary system commands, create or delete files, disable services, and/or execute arbitrary Java code.” reads the advisory published by F5. Pierluigi Paganini.














Let's personalize your content