IBM Cloud inactive identities: Ideas for automated processing
IBM Big Data Hub
SEPTEMBER 29, 2023
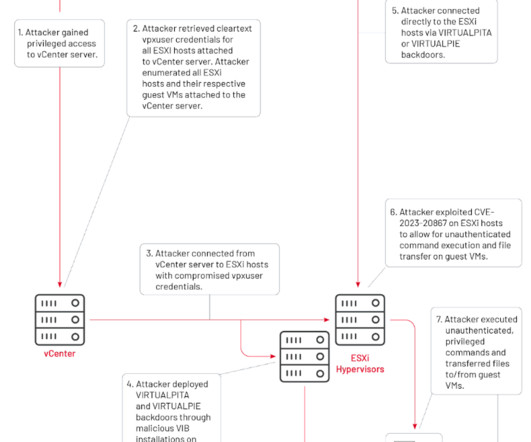
Regular cleanup is part of all account administration and security best practices, not just for cloud environments. When such an identity or an associated API key has not been used to authenticate for a set time, it is considered inactive. The above cleanup steps can be scripted and run manually.

















Let's personalize your content