Experian, You Have Some Explaining to Do
Krebs on Security
JULY 10, 2022
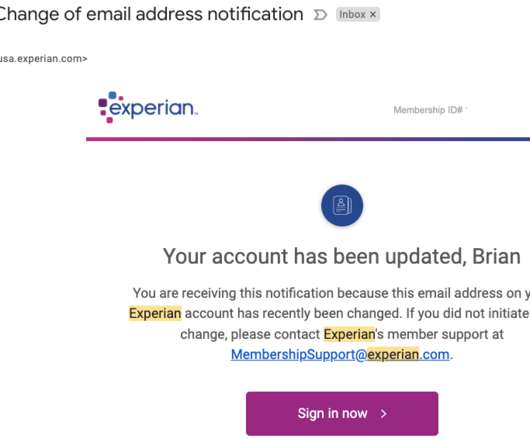
“I was able to answer the credit report questions successfully, which authenticated me to their system,” Turner said. That’s because Experian does not offer any type of multi-factor authentication options on consumer accounts. But now he’s wondering what else he could do to prevent another account compromise.

















Let's personalize your content