How to secure QNAP NAS devices? The vendor’s instructions
Security Affairs
JANUARY 7, 2022
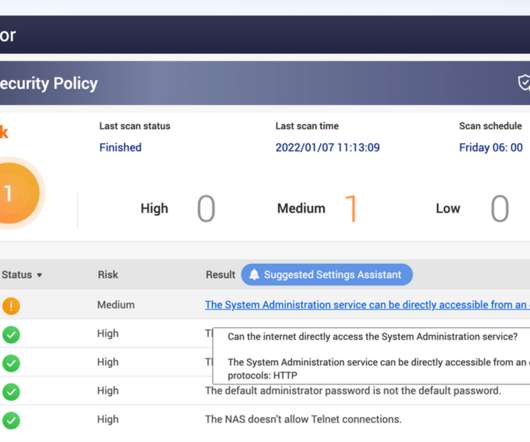
Taiwanese vendor QNAP has warned customers to secure network-attached storage (NAS) exposed online from ransomware and brute-force attacks. QNAP urges all QNAP NAS users to follow the security setting instructions below to ensure the security of QNAP networking devices.” 024 ($1,200) up to.06 06 bitcoins ($3,000).























Let's personalize your content