Hackers hijacked the eScan Antivirus update mechanism in malware campaign
Security Affairs
APRIL 24, 2024
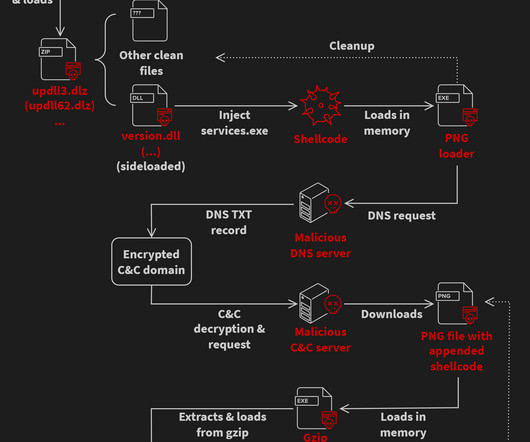
” reads the analysis published by Avast. The issue in the update mechanism was present for at least five years. Puppeteer orchestrates the core functionality of the malware, including the cryptocurrency mining as well as the backdoor deployment. Avast already reported the issue to eScan and the India CERT.




















Let's personalize your content