Researchers Quietly Cracked Zeppelin Ransomware Keys
Krebs on Security
NOVEMBER 17, 2022
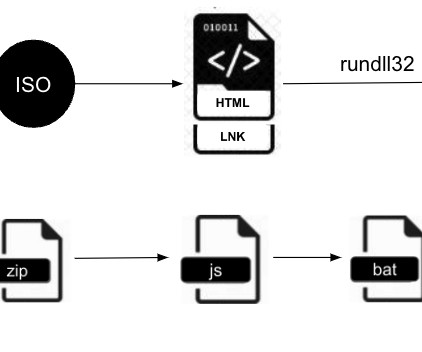
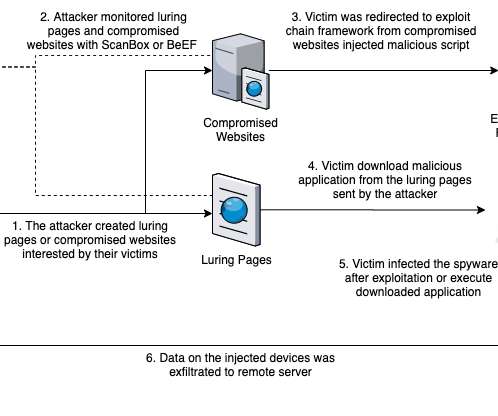
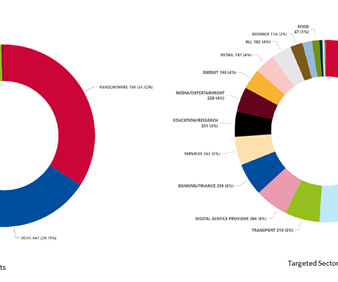
Peter is an IT manager for a technology manufacturer that got hit with a Russian ransomware strain called “ Zeppelin ” in May 2020. He’d been on the job less than six months, and because of the way his predecessor architected things, the company’s data backups also were encrypted by Zeppelin. ” they wrote.

























Let's personalize your content