A brief history of cryptography: Sending secret messages throughout time
IBM Big Data Hub
JANUARY 5, 2024
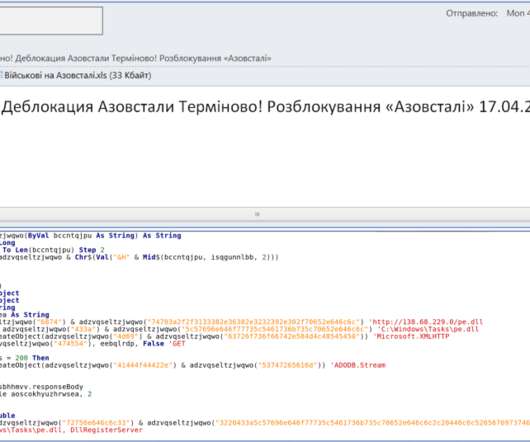
In modern times, cryptography has become a critical lynchpin of cybersecurity. Most cryptosystems begin with an unencrypted message known as plaintext, which is then encrypted into an indecipherable code known as ciphertext using one or more encryption keys. This ciphertext is then transmitted to a recipient.



























Let's personalize your content