GoTrim botnet actively brute forces WordPress and OpenCart sites
Security Affairs
DECEMBER 14, 2022
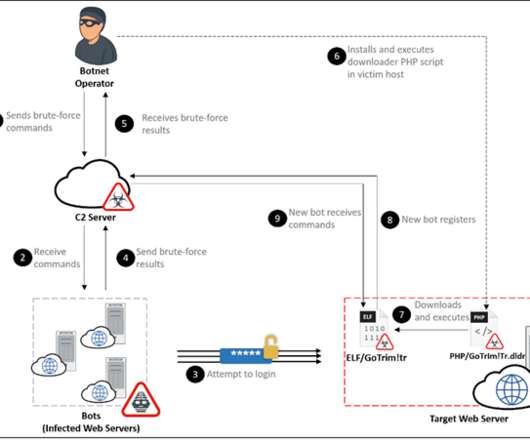
The analysis also revealed that the bot does not maintain persistence in the infected system. C2 communications are encrypted using the Advanced Encryption Standard in Galois Counter Mode (AES-GCM) with a key derived from a passphrase embedded in the malware binary. ” continues the report. ” concludes the report.

















Let's personalize your content