More details about Operation Cronos that disrupted Lockbit operation
Security Affairs
FEBRUARY 20, 2024
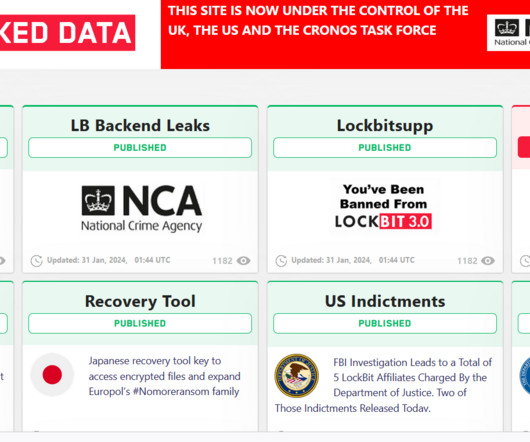
Law enforcement provided additional details about the international Operation Cronos that led to the disruption of the Lockbit ransomware operation. Yesterday, a joint law enforcement action, code-named Operation Cronos , conducted by law enforcement agencies from 11 countries disrupted the LockBit ransomware operation.


















Let's personalize your content