INSIGHTS from SENTINEL
Thales Cloud Protection & Licensing
JUNE 23, 2021
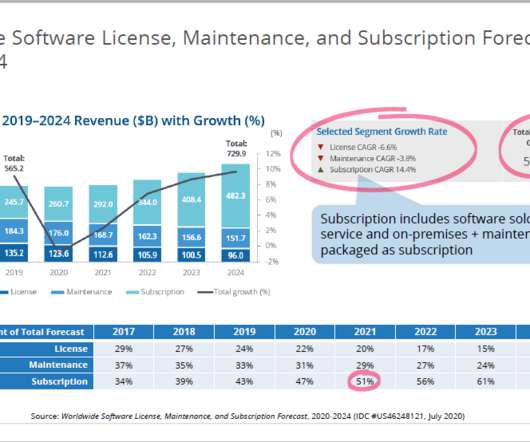
Where Companies Fail and How to Avoid the Traps of Shifting to Subscriptions. Images credit: IDC presentation, Where Companies Fail and How to Avoid the Traps of Shifting to Subscriptions June 2021. . TRANSITIONING TO SUBSCRIPTIONS. Presented by Mark Thomason, IDC Research Director. ?Which Usership vs. Ownership .

















Let's personalize your content