New HiatusRAT campaign targets Taiwan and U.S. military procurement system
Security Affairs
AUGUST 21, 2023
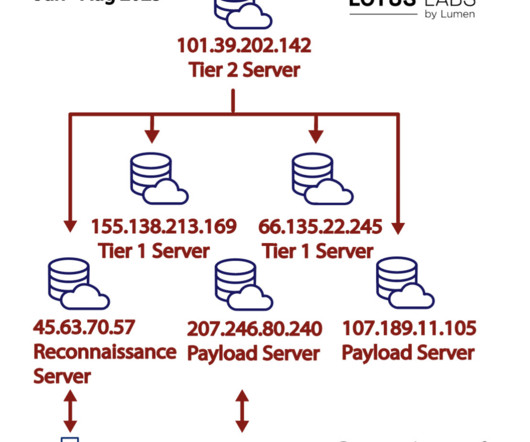
military procurement system. In March 2023, Lumen Black Lotus Labs researchers uncovered a sophisticated campaign called “ HiatusRAT ” that infected over 100 edge networking devices globally. Threat actors leveraged edge routers, or “living on the edge” access, to passively collect traffic and set up a covert C2 infrastructure.















Let's personalize your content