Security Affairs newsletter Round 494 by Pierluigi Paganini – INTERNATIONAL EDITION
Security Affairs
OCTOBER 20, 2024
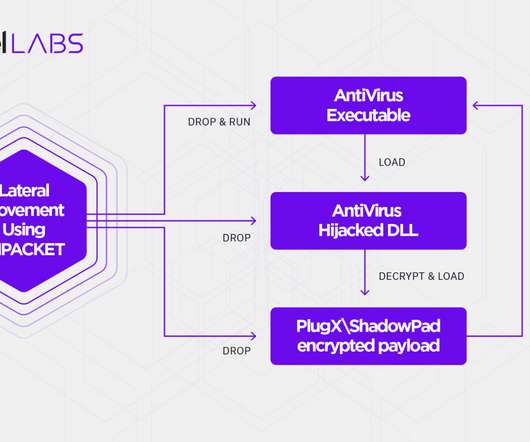
CISA adds Veeam Backup and Replication flaw to its Known Exploited Vulnerabilities catalog North Korea-linked APT37 exploited IE zero-day in a recent attack Omni Family Health data breach impacts 468,344 individuals Iran-linked actors target critical infrastructure organizations macOS HM Surf flaw in TCC allows bypass Safari privacy settings Two Sudanese (..)




































Let's personalize your content