Calendar Meeting Links Used to Spread Mac Malware
Krebs on Security
FEBRUARY 28, 2024
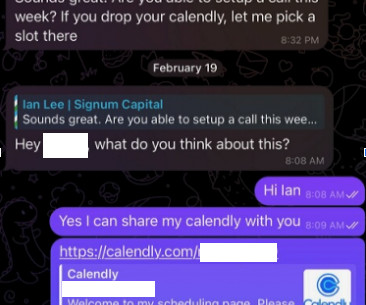
KrebsOnSecurity recently heard from a reader who works at a startup that is seeking investment for building a new blockchain platform for the Web. “When the project team clicks the link, they encounter a region access restriction,” SlowMist wrote.























Let's personalize your content