REvil Ransomware Gang Starts Auctioning Victim Data
Krebs on Security
JUNE 2, 2020
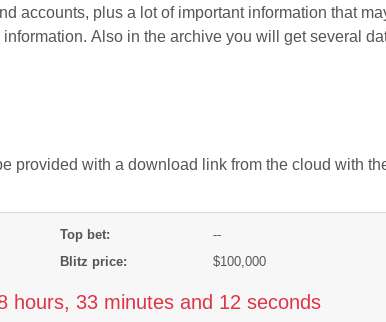
. “ Sodin ” and “ Sodinokibi “) used their Dark Web “Happy Blog” to announce its first ever stolen data auction, allegedly selling files taken from a Canadian agricultural production company that REvil says has so far declined its extortion demands.


















Let's personalize your content