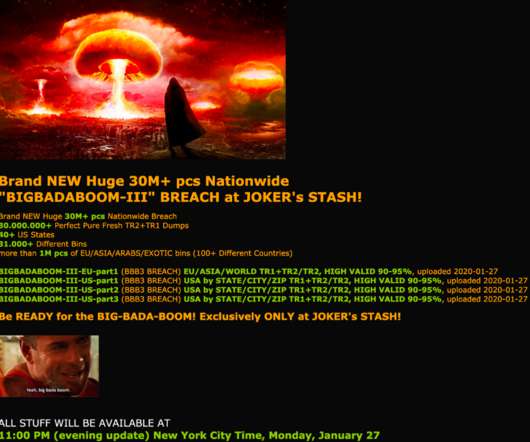
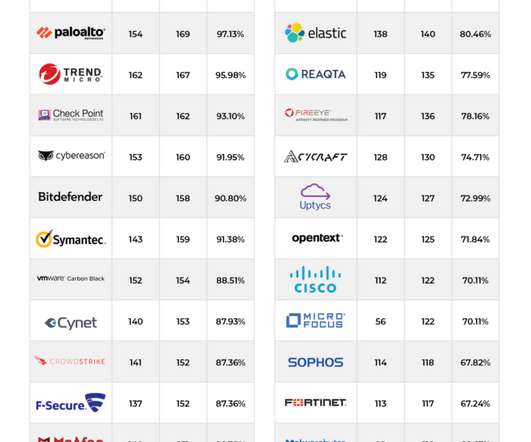
List of data breaches and cyber attacks in March 2020 – 832 million records breached
IT Governance
APRIL 2, 2020
Australia’s Defence Force Recruiting systems were taken offline after security breach (unknown). South African utility provider Eskom is still feeling effects of a cyber security incident (unknown). Wichita State University notifies students and staff of a security incident (1,762). Data breaches. School District (+24).















Let's personalize your content