Microsoft warns of Dexphot miner, an interesting polymorphic threat
Security Affairs
NOVEMBER 26, 2019
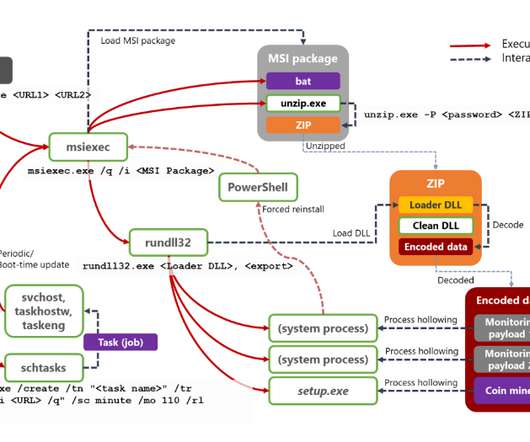
The malicious code abuse of the resources of the infected machine to mine cryptocurrency , according to the experts it has already infected 80,000 computers worldwide. Layers of obfuscation, encryption, and the use of randomized file names hid the installation process. ”reads the analysis published by Microsoft.


















Let's personalize your content