Spotting RATs: Delphi wrapper makes the analysis harder
Security Affairs
JULY 8, 2019
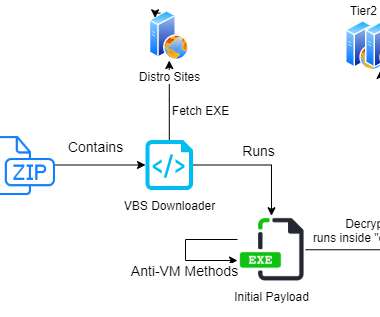
Experts observed an increase of the malware spreading using less-known archive types as dropper,in particular ISO image.Delphi wrapper makes analysis harder. Technical Analysis. As expected, the malicious payload is stored in the resource section in encrypted way (probably using a simple XOR-encryption). Introduction.



























Let's personalize your content