Giving a Face to the Malware Proxy Service ‘Faceless’
Krebs on Security
APRIL 18, 2023
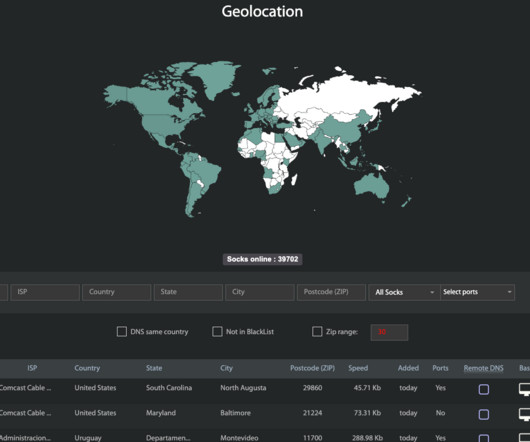
Kilmer said when Spur first started looking into Faceless, they noticed almost every Internet address that Faceless advertised for rent also showed up in the IoT search engine Shodan.io Those with IoT zero-days could expect payment if their exploit involved at least 5,000 systems that could be identified through Shodan.












Let's personalize your content