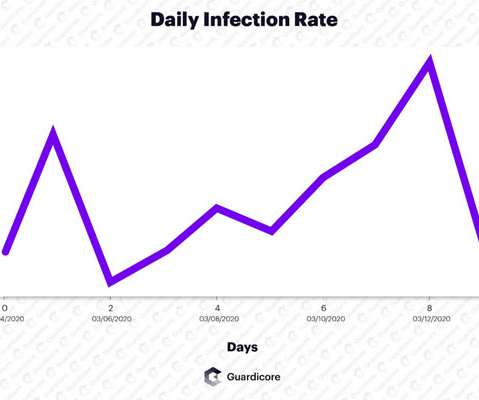
Vollgar botnet has managed to infect around 3k MSSQL DB servers daily
Security Affairs
APRIL 1, 2020
Cybersecurity researchers spotted a crypto-mining botnet, tracked as Vollgar, that has been hijacking MSSQL servers since at least 2018. Researchers at Guardicore Labs discovered a crypto-mining botnet , tracked as Vollgar botnet , that is targeting MSSQL databases since 2018. ” reads the analysis published by Guardicore.













Let's personalize your content