Financially motivated Earth Lusca threat actors targets organizations worldwide
Security Affairs
JANUARY 18, 2022
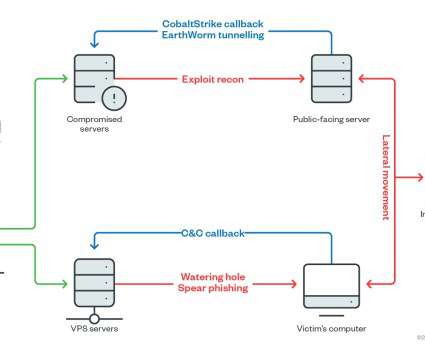
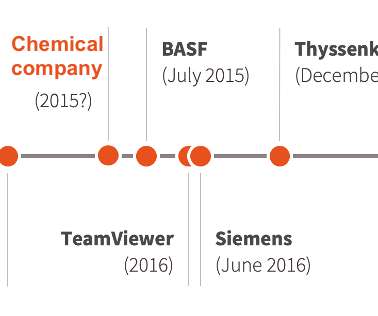
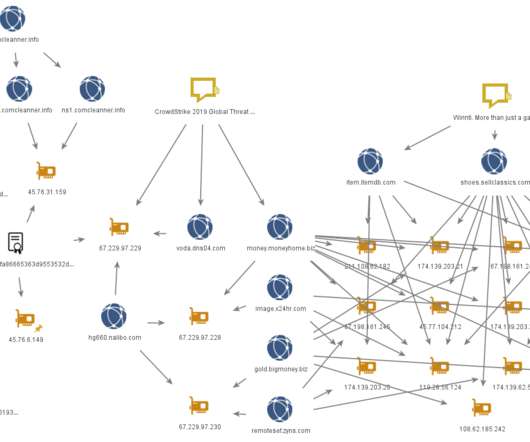
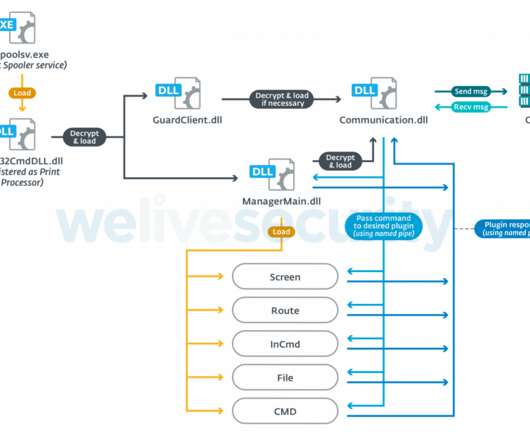
According to the security firm, the group is financially motivated, its cyberespionage campaign hit high value targets such as government and educational institutions, religious movements, pro-democracy and human rights organisations in Hong Kong, Covid-19 research organisations, gambling and cryptocurrency companies, and the media.















Let's personalize your content