Expert identifies new Nazar APT group referenced in 2017 Shadow Brokers leak
Security Affairs
APRIL 23, 2020
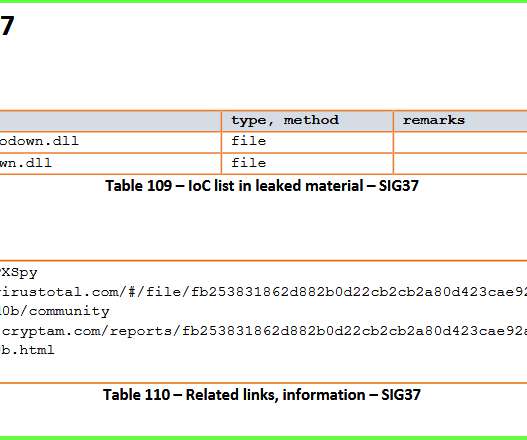
A security expert uncovered an old APT operation, tracked Nazar, by analyzing the NSA hacking tools included in the dump leaked by Shadow Brokers in 2017. The name ‘Nazar’ comes from the debug paths he found in the dump alongside Farsi resources in some of the malware droppers. ” reads a blog post published by Guerrero-Saade.















Let's personalize your content