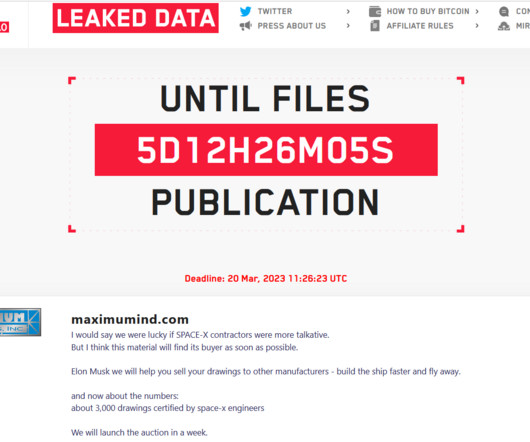
Key aerospace player Safran Group leaks sensitive data
Security Affairs
MARCH 15, 2023
It collaborates with Airbus, the second-largest aerospace company globally after Boeing, to manufacture aerospace equipment. Also, the company manufactures surface-to-air defense systems and missiles. It is crucial to ensure that leaked keys are in longer bit-lengths and encoded using secure encryption/hashing algorithms.












Let's personalize your content