FBI: Operation ‘Duck Hunt’ dismantled the Qakbot botnet
Security Affairs
AUGUST 30, 2023
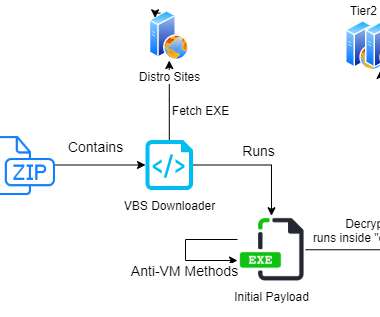
’ Qakbot , also known as QBot, QuackBot and Pinkslipbot, is an info-stealing malware that has been active since 2008. “The victims ranged from financial institutions on the East Coast to a critical infrastructure government contractor in the Midwest to a medical device manufacturer on the West Coast.”

























Let's personalize your content