New QBot campaign delivered hijacking business correspondence
Security Affairs
APRIL 17, 2023
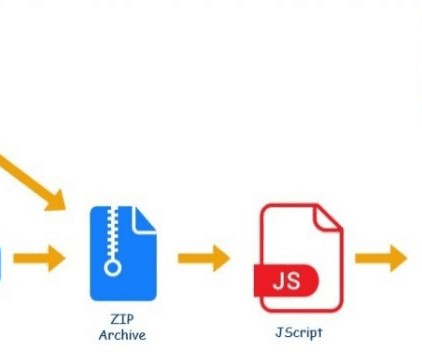
QBot has been active since 2008, it is used by threat actors for collecting browsing data and banking credentials, and other financial information from the victims. The threat actors behind the campaign observed by Kaspersky used e-mail written in different languages, including English, German, Italian, and French.



















Let's personalize your content