Zimbra urges customers to manually fix actively exploited zero-day reported by Google TAG
Security Affairs
JULY 13, 2023
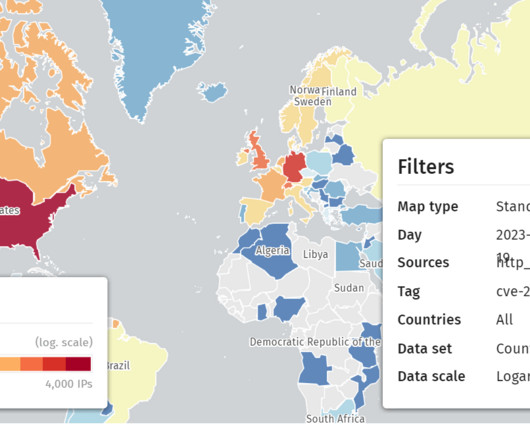
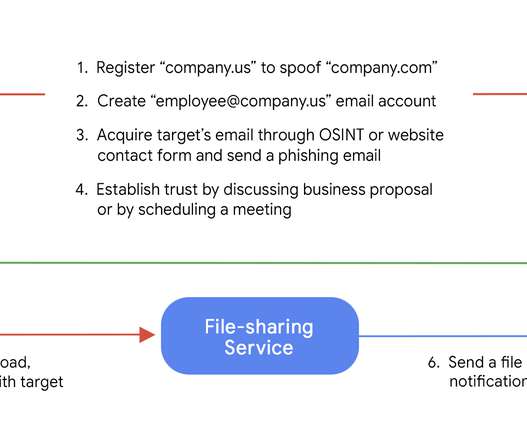
Zimbra has released updates to address a zero-day vulnerability actively exploited in attacks aimed at Zimbra Collaboration Suite (ZCS) email servers. Zimbra urges customers to manually install updates to fix a zero-day vulnerability that is actively exploited in attacks against Zimbra Collaboration Suite (ZCS) email servers.

































Let's personalize your content