Dead System Admin's Credentials Used for Ransomware Attack
Data Breach Today
JANUARY 28, 2021
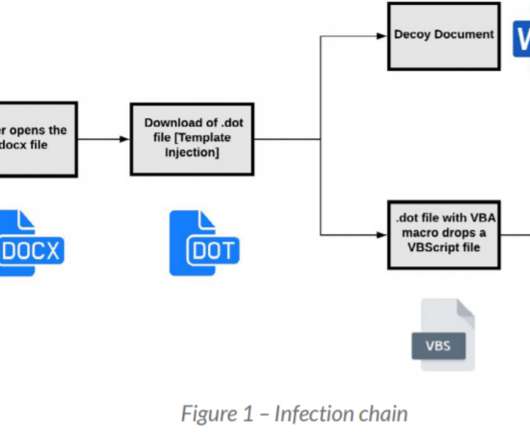
Sophos: 'Ghost' Accounts Present a Potential Security Danger The operators of the Nefilim ransomware used the credentials of a deceased system administrator to plant their crypto-locking malware in about 100 vulnerable systems during one attack, according to Sophos.






















Let's personalize your content