Panasonic Warns That IoT Malware Attack Cycles Are Accelerating
WIRED Threat Level
AUGUST 9, 2023
The legacy electronics manufacturer is creating IoT honeypots with its products to catch real-world threats and patch vulnerabilities in-house.

WIRED Threat Level
AUGUST 9, 2023
The legacy electronics manufacturer is creating IoT honeypots with its products to catch real-world threats and patch vulnerabilities in-house.

Thales Cloud Protection & Licensing
FEBRUARY 28, 2022
To enable this revolution, automobile manufacturers and their supply chain partners have rapidly adopted new technologies to better serve customers and win competitive advantages: Embedding high-speed connectivity in vehicles to improve customer experience and entertainment as well as real-time diagnostics and OTA updates.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JUNE 22, 2019
The malicious code attempt to determine if it is running in a honeypot , then it downloads the payload and changes its permission settings to allow its execution. In order to determine what miner to deliver, the bot collects system information, such as manufacturer, hardware details, and processor architecture. The script for a.

Security Affairs
APRIL 28, 2020
The purpose of the script is to optimize the mining module by querying the information about the CPU through the reading of the “ /proc/cpu ” and when the manufacturer is retrieved the script provides to add some specific registry values depending by the vendor through the Model-Specific Register utility “ wrmsr ”.
Security Affairs
MAY 12, 2021
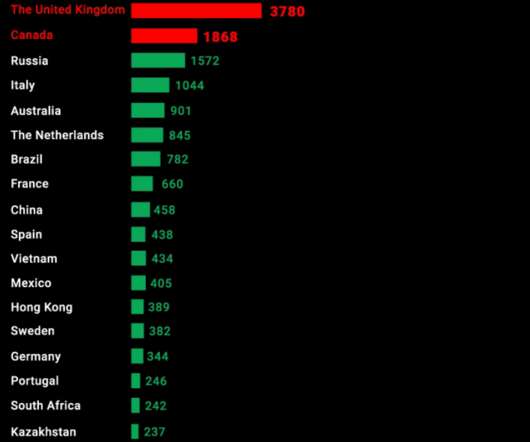
Our research shows that large and small manufacturers are identifiable, with Aastra-Mitel topping the list. Aastra-Mitel tops the manufacturer list, the United States leads the list among countries, and London tops the chart among cities. Devices made by the US manufacturer Polycom, a subsidiary of Plantronics Inc., What we did.

Security Affairs
SEPTEMBER 30, 2019
But let’s go back to the beginning of the story when my very good friend @0xrb found in his honeypot this new “ Mirai like ” Linux malware, which has important differences with the Mirai implementation. The beginning of the story: another IoT malware in the wild?

eSecurity Planet
MARCH 23, 2022
Manufactured BackDoor Vulnerabilities. For example, a honeypot data server can be established with an enticing name such as “Research Archive” or “Financial Records” and alerts can be generated as soon as an attacker attempts to explore the contents. Also read: Top Vulnerability Management Tools.
Let's personalize your content