RSAC insights: Software tampering escalates as bad actors take advantage of ‘dependency confusion’
The Last Watchdog
JUNE 3, 2022
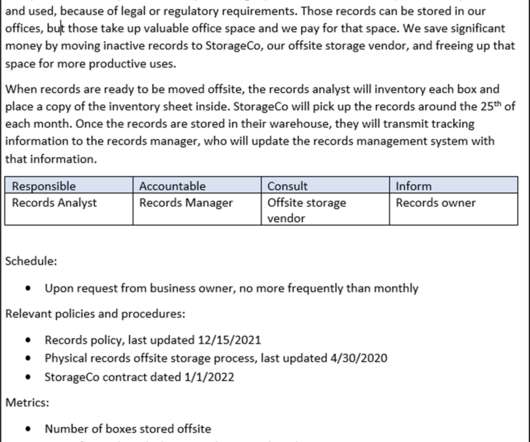
Its function is to record events in a log for a system administrator to review and act upon. Left unpatched, Log4Shell, presents a ripe opportunity for a bad actor to carry out remote code execution attacks, Pericin told me. In the current, operating environment, there’s limitless opportunity to tamper with code.

















Let's personalize your content