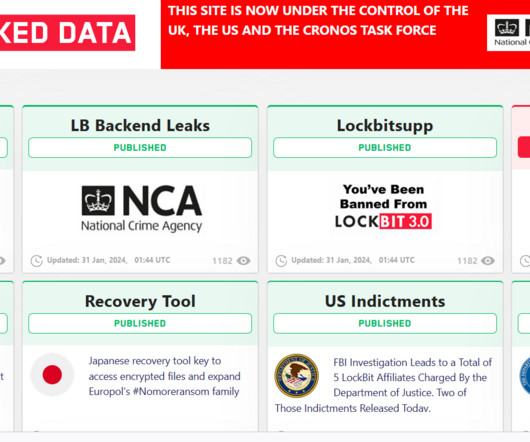
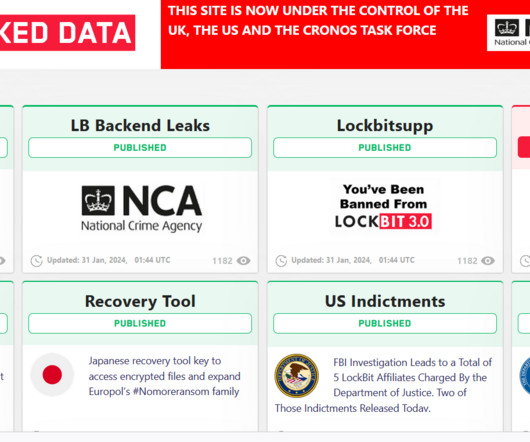
Operation Cronos: law enforcement disrupted the LockBit operation
Security Affairs
FEBRUARY 19, 2024
Since January 2020, affiliates utilizing LockBit have targeted organizations of diverse sizes spanning critical infrastructure sectors such as financial services, food and agriculture, education, energy, government and emergency services, healthcare, manufacturing, and transportation. on January 5, 2020.














Let's personalize your content