Microsoft Fully Ditches the Password
Data Breach Today
SEPTEMBER 15, 2021
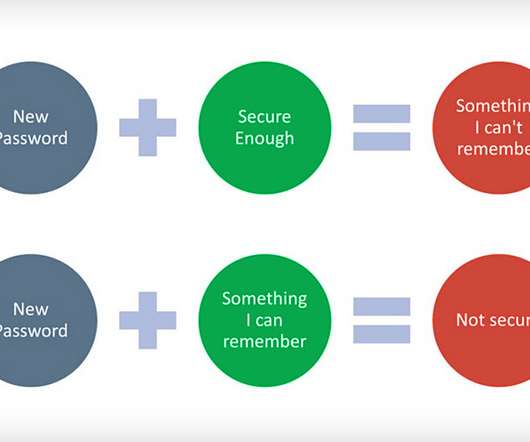
Windows Users Can Now Use Other Methods to Access Microsoft Products Microsoft has officially gone fully passwordless, allowing Windows users to replace their alphanumeric passwords with one of several substitute sign-in technologies to gain entry into a Microsoft product - a move received positively by industry insiders.




































Let's personalize your content