Medical Debt Collection Firm R1 RCM Hit in Ransomware Attack
Krebs on Security
AUGUST 14, 2020
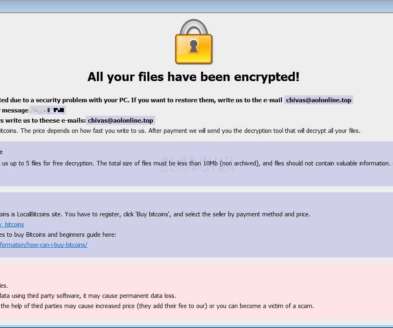
R1 RCM Inc. [ NASDAQ:RCM ], one of the nation’s largest medical debt collection companies, has been hit in a ransomware attack. Formerly known as Accretive Health Inc. , Chicago-based R1 RCM brought in revenues of $1.18 billion in 2019. The company has more than 19,000 employees and contracts with at least 750 healthcare organizations nationwide.





































Let's personalize your content