City Pays Ransom Despite Pre-Ransomware Outbreak Hack Alert
Data Breach Today
JUNE 12, 2020
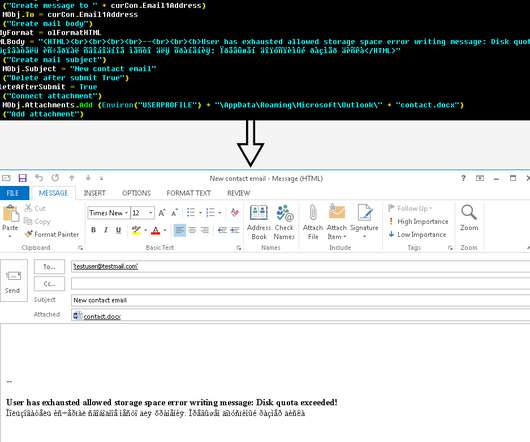
DoppelPaymer Hit Comes as Ransomware Attacks - and Data-Leaking Shakedowns - Surge The attack sounds ripped from an episode of TV show "24": Hackers have infiltrated a government network, and they're days away from unleashing ransomware. Unfortunately for Florence, a city in Alabama, no one saved the day, and officials are sending $300,000 in bitcoins to attackers for a decryption key.







































Let's personalize your content