Breach of COVID-19 Test Data Undermines Pandemic Response
Data Breach Today
SEPTEMBER 15, 2020
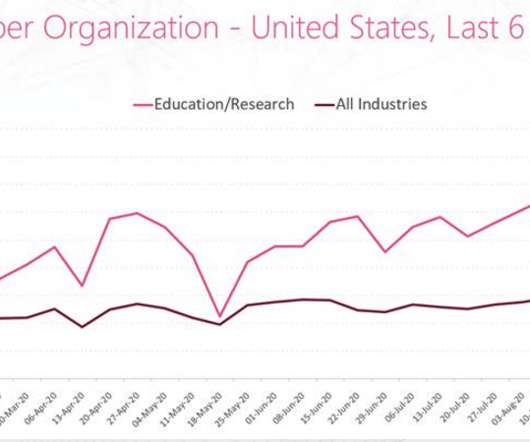
'Human Error' Results in 18,000 Individuals' Test Results Being Exposed in Wales What's one of the worst things that can happen during a pandemic? The answer is anything that gives people less reason to trust in their public health system to handle the crisis. Enter a data breach that has exposed personal information for everyone who's ever tested positive for the disease in Wales.







































Let's personalize your content