New Phishing Attack Attempts to Steal Social Security Numbers
KnowBe4
OCTOBER 20, 2022
A phishing campaign is impersonating the US Social Security Administration (SSA) in an attempt to steal Social Security numbers, according to researchers at INKY.

KnowBe4
OCTOBER 20, 2022
A phishing campaign is impersonating the US Social Security Administration (SSA) in an attempt to steal Social Security numbers, according to researchers at INKY.
Krebs on Security
OCTOBER 20, 2022
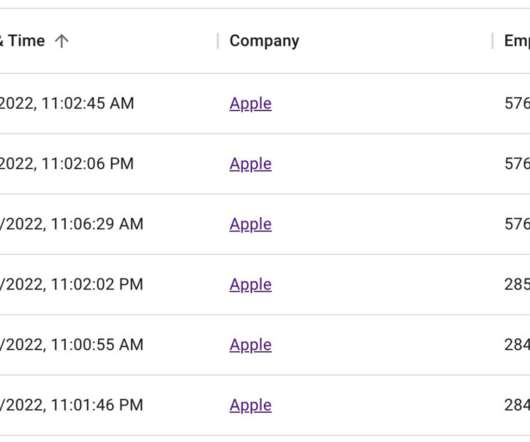
On October 10, 2022, there were 576,562 LinkedIn accounts that listed their current employer as Apple Inc. The next day, half of those profiles no longer existed. A similarly dramatic drop in the number of LinkedIn profiles claiming employment at Amazon comes as LinkedIn is struggling to combat a significant uptick in the creation of fake employee accounts that pair AI-generated profile photos with text lifted from legitimate users.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Data Breach Today
OCTOBER 20, 2022
FurBall Android Malware Accesses Smartphone Contacts, Say Eset Researchers Researchers from cybersecurity firm Eset found a variant of Android stalkerware dubbed FurBall slightly modified in a semi-successful bid to evade detection. The malware, dubbed FurBall, is a tool used by a hacking group linked to the Iranian government.

Security Affairs
OCTOBER 20, 2022
Cybersecurity researchers warn of a new PowerShell backdoor that disguises itself as part of the Windows update process to avoid detection. Cybersecurity researchers from SafeBreach a warning of a new PowerShell backdoor masqueraded as a Windows update process to avoid detection. The backdoor spreads via weaponized Word documents (“ Apply Form.docm.”) posing as a LinkedIn-based job application.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Data Breach Today
OCTOBER 20, 2022
The latest edition of the ISMG Security Report discusses how Russian-speaking ransomware gangs have their eyes on a new target, offers the latest on Australia's data security reckoning and the government’s response, and outlines emerging trends in customer identity and access management.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
OCTOBER 20, 2022
Customer Convenience, Not Security, Should Be the Selling Point for FIDO Passkeys Organizations can improve security with modern authentication protocols, but the big message to the marketplace is that FIDO Passkeys give customers more convenience and deliver a consistent user experience, according to panelists on the final day of FIDO Alliance's Authenticate 2022 Conference.

eSecurity Planet
OCTOBER 20, 2022
Cloud security builds off of the same IT infrastructure and security stack principles of a local data center. However, a cloud vendor offering provides a pre-packaged solution that absorbs some operational and security responsibilities from the customer. Exactly which responsibilities the cloud vendor absorbs depends upon the type of solution. While cloud security offerings provide a wide spectrum of choices, there are three generalized situations to compare against on-premises data centers: inf

Data Breach Today
OCTOBER 20, 2022
Suspect Accused of Lead Role in Disrupting Coronavirus Vaccination Data in December The Federal Police of Brazil arrested a lead suspect behind a December 2021 incident that temporarily disrupted access to novel coronavirus vaccination data. The suspect, arrested in the city of Feira de Santana, is an alleged member of the multinational and teenager-dominated Lapsus$ hacking group.

Security Affairs
OCTOBER 20, 2022
Healthcare system Advocate Aurora Health (AAH) disclosed a data breach that exposed the personal data of 3,000,000 patients. The US-based hospital healthcare system Advocate Aurora Health (AAH) disclosed a data breach that exposed the personal data of 3,000,000 patients. The company is notifying the impacted individuals. The healthcare system operates 26 hospitals in Wisconsin and Illinois.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
OCTOBER 20, 2022
Dharma, Crylock and Thanos Most Active, OldGremlin Most Greedy, Researchers Find More Russian-speaking, ransomware-wielding attackers are gunning for Russian businesses and government agencies, researchers report. The unwritten rule of Russian cybercrime has historically been to never attack inside Russia or neighboring allies.

Data Matters
OCTOBER 20, 2022
The U.S. Treasury Department is seeking public comment on the need and scope for a potential federal insurance response to catastrophic cyber incidents, akin to the one put in place for terrorism insurance after the attacks of September 11, 2001. In its request for comment , the agency is seeking public input until November 14, 2022 on whether risks to critical infrastructure stemming from catastrophic cyberattacks “warrant a federal insurance response.

Data Breach Today
OCTOBER 20, 2022
Minister for Home Affairs O'Neil Likens Hackers to Dogs Australia's largest private health insurer has transformed over a week from being confident that it repelled a cyber incident to being apologetic after disclosing that hackers got away with up to 200 gigabytes of customer data. Australian Federal Police are investigating the incident at Medibank.
Security Affairs
OCTOBER 20, 2022
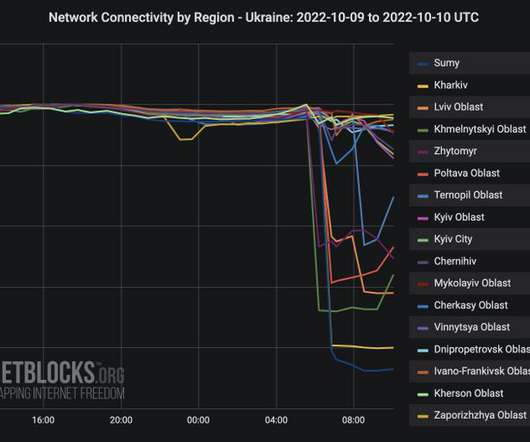
While the Russian army is conducting coordinated missile and drone strikes in Ukraine experts observed Internet disruptions in the country. Starting on the morning of Monday, October 10, the Russian army is targeting several cities in Ukraine with coordinated missile and drone strikes. The escalation is a retaliation for the bombing of a bridge connecting Crimea to Russia.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
OCTOBER 20, 2022
Fraud Expert Shares Tactics, Trends on Check Washing, Zelle Scams, Mobile ID Theft Fraudsters are using tried-and-true tactics such as check washing as well as Zelle scams and a host of insider threats to scam banks and their customers. Frank McKenna, chief fraud strategist at Point Predictive and author, explains why fraud is on the rise and the steps banks can take to stop it.

Dark Reading
OCTOBER 20, 2022
Many enterprises continue to leave cloud storage buckets exposed despite widely available documentation on how to properly secure them.

Data Breach Today
OCTOBER 20, 2022
Medibank Extortionists Prove Their Hack and Vinomofo Data Turns Up on Forum Australia's data breach debacle expanded on Thursday. Cyber extortionists who attacked Australian health insurer Medibank provided proof of their hack of medical data. Also, stolen data from Australian wine retailer Vinomofo was put up for sale on a Russian-language forum.

Dark Reading
OCTOBER 20, 2022
Zero trust protects identities, endpoints, applications, networks, infrastructure, and data, and can be implemented in different ways.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

KnowBe4
OCTOBER 20, 2022
Compliance training is often seen as a chore that organizations need to just get through. That said, compliance cannot simply be ignored. A recent report from software firm GlobalScape found that organizations lose an average of $4 million in revenue due to just one non-compliance event. Yikes! In our 2022 State of Employee Compliance Training report , we compiled the top challenges faced by compliance training managers.

Dark Reading
OCTOBER 20, 2022
CISOs and security leaders in state and local governments are dealing with increasing threats like ransomware — with varying degrees of cyber maturity.
Security Affairs
OCTOBER 20, 2022
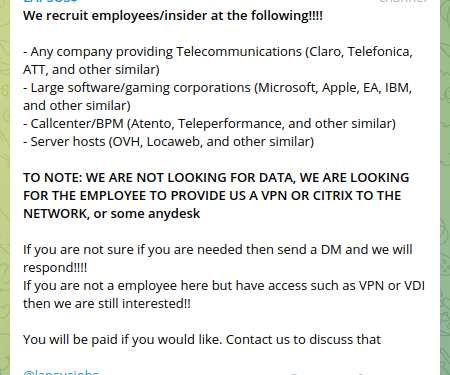
The Federal Police of Brazil arrested an individual who is suspected of being a member of the notorious LAPSUS$ extortionist group. The Federal Police of Brazil yesterday announced the arrest of an individual suspected of being linked to the LAPSUS$ extortionist gang. The authorities did not disclose info about the individual, it seems that the suspect is a teenager.

Dark Reading
OCTOBER 20, 2022
Achieving basic IT hygiene is 99% of the game.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Data Matters
OCTOBER 20, 2022
The U.S. Treasury Department is seeking public comment on the need and scope for a potential federal insurance response to catastrophic cyber incidents, akin to the one put in place for terrorism insurance after the attacks of September 11, 2001. The post U.S. Treasury Department Seeks Public Comment On Potential Federal Cyber Insurance Program appeared first on Data Matters Privacy Blog.

Dark Reading
OCTOBER 20, 2022
New Android malware variant is part of long-running Domestic Kitten campaign being conducted by APT C-50 Group, analysts report.

WIRED Threat Level
OCTOBER 20, 2022
Vice Society has a superpower that’s allowed it to quietly carry out attacks on schools and hospitals around the world: mediocrity.

Dark Reading
OCTOBER 20, 2022
The new open source specification from Open Compute Project is backed by Google, Nvidia, Microsoft, and AMD.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Zapproved
OCTOBER 20, 2022
More than 90% of civil cases are settled before they ever go to trial. Still, companies have no way of knowing whether a given matter will fall into that 10% that do proceed to trial. That’s why your organization must take every triggering event seriously. When the possibility of litigation arises and the discovery process […].

Dark Reading
OCTOBER 20, 2022
Feeling creative? Submit your caption and our panel of experts will reward the winner with a $25 Amazon gift card.

Jamf
OCTOBER 20, 2022
Learn about how the partnership between Jamf and Red Canary can accelerate the security of your organization’s Apple fleet, helping your IT and Security teams to work smarter, not harder to identify, detect and remediate threats to your devices, users and data.
Let's personalize your content