AvosLocker ransomware now targets Linux systems, including ESXi servers
Security Affairs
JANUARY 11, 2022
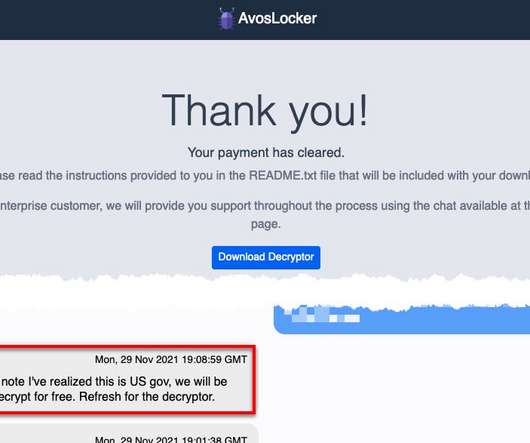
AvosLocker is the latest ransomware that implemented the capability to encrypt Linux systems including VMware ESXi servers. AvosLocker expands its targets by implementing the support for encrypting Linux systems, specifically VMware ESXi servers, Bleeping computed reported. “While we couldn’t find what targets were attacked using this AvosLocker ransomware Linux variant , BleepingComputer knows of at least one victim that got hit with a $1 million ransom demand.” reported Blee








































Let's personalize your content