Colonial Pipeline Starts Recovery from Ransomware
Data Breach Today
MAY 10, 2021
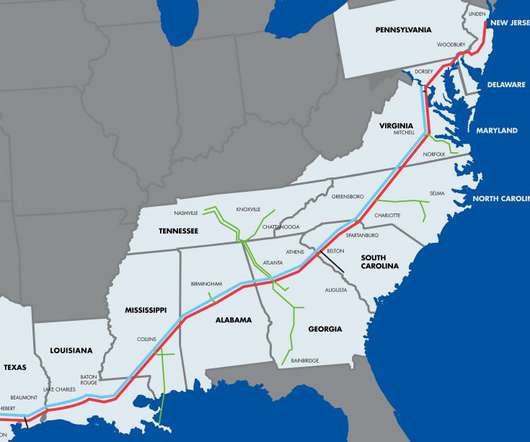
Report: DarkSide Ransomware Gang Infected Fuel Supplier Colonial Pipeline Company has restored smaller pipelines that ship fuels to the U.S. East Coast after a ransomware incident, but its larger ones are still offline as it assesses safety. Citing U.S. officials, the Associated Press reports the company was infected by the DarkSide ransomware group.









































Let's personalize your content